Are you an SJO, human rights defender, or activist frustrated by digital restrictions keeping you from accessing the internet and social media for your work? You are not alone—many civil society members in the Global South face internet censorship challenges that prevent them from communicating with their communities and accessing information/apps relevant to their work.
So what is Censorship? It is the deliberate suppression or restriction of access to information or content typically done by governments, organizations, or other authoritative bodies. This can apply to information in all forms, including print, digital, and broadcast media, and can take different forms from blocking websites to manipulating search results. Censorship aims to control or influence public perceptions and behavior for several reasons including maintaining political stability, protecting national security, preventing the spread of misinformation, or upholding cultural and moral standards. While many governments argue that censorship is necessary to restrict content for national security, censorship often violates fundamental human rights in the digital space including access to information, freedom of expression, right to privacy, and freedom of the press, among others.
There are several tools and settings that you can configure to navigate internet restrictions, ranging from using a VPN to mask your location, a proxy server to act as a digital bridge, or tweaking your DNS settings. For additional privacy, you can use privacy browsers like the Tor Browser to secure all your browsing activity while accessing content restricted in your region.
- Accessing the Internet Through Mobile Data: Switching to mobile data may help bypass some restrictions imposed by your Internet Service Provider. Disable Wi-Fi on your device then enable cellular data and attempt to access a restricted website or application. If this does not work, you can try any of the following methods below:
2. USING A VPN
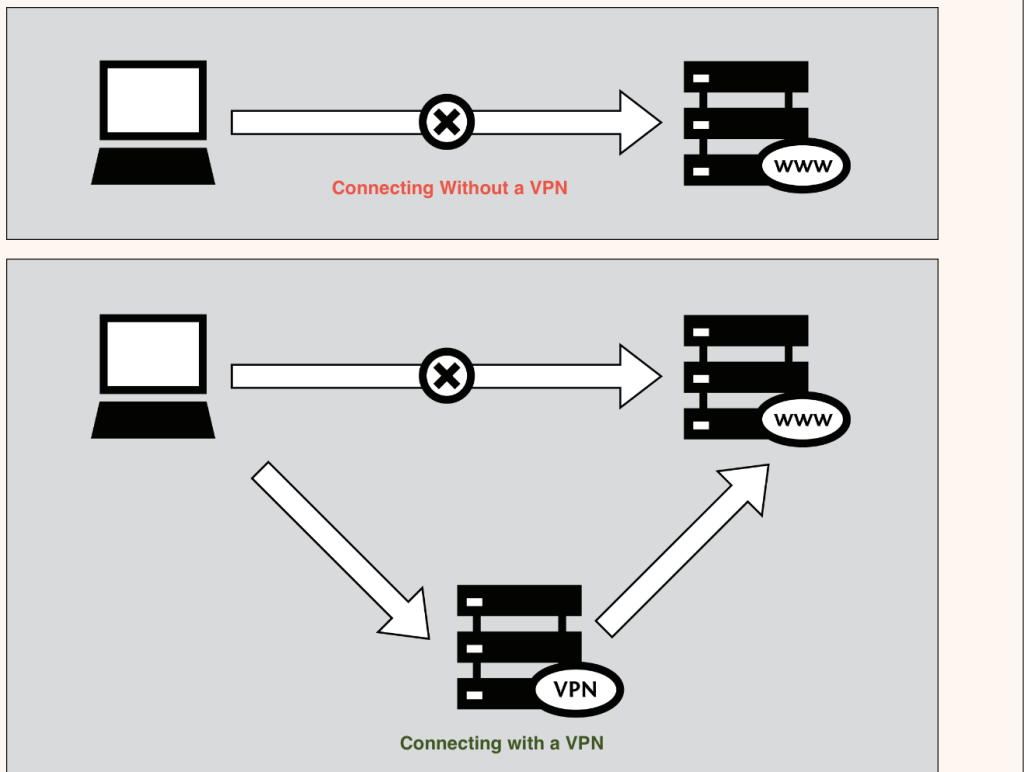
When properly configured, a Virtual Private Network (VPN) can help you bypass the following internet restriction mechanisms:
- Deep packet inspection: Internet providers and governments can inspect data as it passes through the Internet and block activity associated with specific keywords, search terms, or protocols. A VPN encrypts your internet traffic which makes it difficult to examine therefore allowing you to access websites and content that would otherwise be blocked.
- DNS tampering and poisoning: The Domain Name System is responsible for translating the human-readable domain names (website names) to their respective IP addresses. When tampered with users are redirected to incorrect IP addresses therefore denying them access to the intended content. For example, a user trying to access information from tatua.digital might be redirected to an error page or a similar-looking website whose content is heavily controlled by the government. Using a VPN can help bypass such controls since the user’s internet traffic is encrypted and therefore inaccessible for manipulation.
- IP address blocking and Blacklisting: This is where (a) IP addresses associated with specific websites and services are blocked therefore preventing users from accessing them or (b) users with IP addresses from specific locations are blocked from accessing websites and services. VPNs redirect traffic through their servers before they reach the destination sometimes even routing through servers in different countries. This hides the fact that the request is coming from an IP address in a blocked location or that it is coming from a blocked destination therefore allowing users to access restricted content.
- Bandwidth throttling: Censors may not block access entirely but can restrict the bandwidth for certain types of traffic resulting in slow internet speeds. This can discourage users from accessing specific content or using certain services like specific social media apps. Some VPNs use obfuscation methods to disguise VPN traffic as regular HTTPS traffic, making it harder for censors to detect and block/slow down. For example, using the Obfsproxy or Stunnel protocol can make VPN traffic appear as standard web traffic therefore blocking bandwidth-related censorship.
Here is a list of VPNs that you can download and configure yourself or contact Tatua to help you set up:
- TunnelBearVPN
- Psiphon VPN
- NordVPN
- RiseupVPN
- ProtonVPN
- OpenVPN
- ExpressVPN
- Surfshark
Configuration Steps:
- Download the VPN application from its official website.
- Install and open the app.
- Sign in or create an account.
- Choose a server location outside of your country or continent.
- Connect and verify that you can access the restricted app or website.
NOTE: While VPNs are powerful tools for circumventing censorship, it is important to remember that are not foolproof. Advanced censors may still find ways to block VPN traffic, especially if they control the internet infrastructure. Additionally, an improperly configured VPN can still expose you to censorship, and using a VPN in certain countries can be illegal. Users should always be aware of the legal risks involved and choose VPN services that are known for their reliability and commitment to privacy.
3. USING A PROXY SERVER
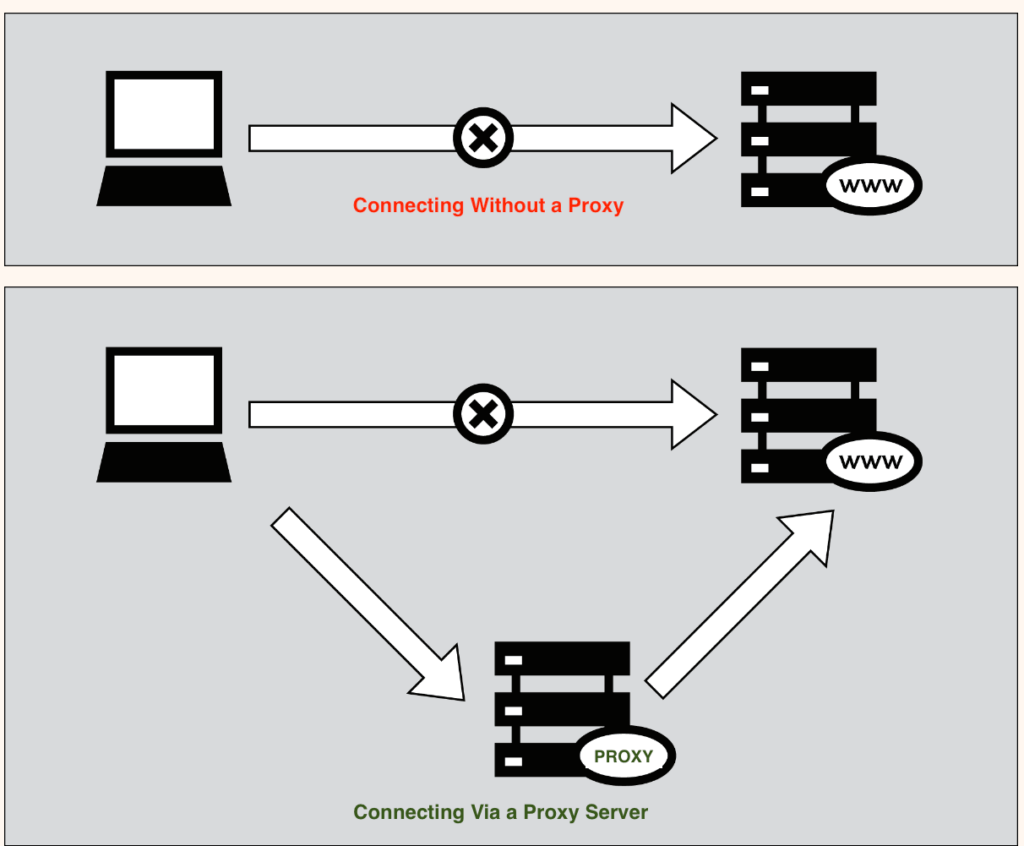
A proxy server is an intermediary between a user’s device and the internet, and it can be used to bypass censorship in several ways. When you connect to a website or online service through a proxy server, your request first goes to the proxy server, which then forwards it to the destination server (the website or service you want to access). The response from the destination server is sent back to the proxy, which then forwards it to you. This means that the destination server sees the request as coming from the proxy server’s IP address rather than your own. This basic mechanism is key to how proxies can help bypass censorship. Proxy servers can help bypass censorship through the following mechanisms:
- IP address masking: When you use a proxy, the destination website or service reads the request as coming from the IP address of the proxy server instead of your device which can help access content that would otherwise be restricted to your device’s IP address or location.
- Bypassing blocklists: Using a proxy can help you access content if your device is in a blocklist since connections appear to be coming from the proxy server which may not be on a government or ISP blocklist.
- Bypassing local network restrictions: In environments like schools, workplaces, or public Wi-Fi networks, certain websites or services might be restricted. A proxy server can help bypass these local network restrictions by rerouting your internet traffic through the proxy, making it appear as though you’re accessing a permitted site.
Here is a list of some Proxy Services you can check out:
- Hide.me Proxy
- KProxy
- Proxysite
Configuration: Visit the proxy service’s website and follow the instructions on how to configure the service to access restricted content
While proxy servers can be effective tools for bypassing censorship, they do have limitations:
- Limited Encryption: Most proxy servers do not encrypt the traffic between the user and the proxy, which means that while the destination might be hidden, the content of your traffic could still be inspected by censors.
- Proxy Detection and Blocking: Some advanced censorship systems can detect and block proxy traffic, especially if the proxy server is well-known or frequently used.
- Performance Issues: Using a proxy can slow down your internet connection, particularly if the proxy server is located far from your location or is overloaded with requests.
- Security Risks: Not all proxy servers are trustworthy. Some may log your activity or inject ads or malware into your traffic, posing security risks.
- Security Risks: Not all proxy servers are trustworthy. Some may log your activity or inject ads or malware into your traffic, posing security risks.
4. CHANGING YOUR DNS SETTINGS
Changing your device’s DNS (Domain Name System) settings can be a simple yet effective way to bypass censorship. The DNS is like the internet’s phone book, translating domain names like tatua.digital into IP addresses that computers use to locate and connect to websites. By changing your DNS settings, you can avoid censorship mechanisms that rely on the following DNS filtering or blocking mechanisms.
- Blocking DNS Requests: Censors can configure DNS servers to block requests for specific domains. When a user tries to access a censored website, the DNS server either fails to return an IP address or redirects the user to a different page.
- DNS Redirection: Instead of blocking a request, the DNS server might redirect users to a government-approved page or a warning page that explains why the site is blocked.
- Manipulating DNS Records: Censors can manipulate DNS records to point to a different IP address, leading users to fake or misleading versions of prohibited websites.
You can change your DNS settings to use a DNS server that isn’t controlled by your ISP or government, therefore bypassing the DNS filtering or blocking imposed by these authorities. Common options include:
- Using public DNS Servers: Services like Google Public DNS (8.8.8.8 and 8.8.4.4) or Cloudflare DNS (1.1.1.1) provide free and uncensored DNS resolution, allowing you to access blocked websites.
- Using third-party DNS Services: There are many other third-party DNS services, such as OpenDNS, Quad9, and others, that offer uncensored DNS lookups and may provide additional features like phishing protection or content filtering (which can be disabled if you want full access).
How to change your DNS settings
- On Windows
- Open Network Settings: Go to Control Panel > Network and Internet > Network and Sharing Center > Change adapter settings.
- Right-click on your active network connection and select “Properties.”
- Select “Internet Protocol Version 4 (TCP/IPv4)” and click “Properties.” In the next window, select “Use the following DNS server addresses” and enter the DNS addresses you want to use (e.g., 8.8.8.8 and 8.8.4.4 for Google DNS).
- Click “OK” to save your settings.
- ON MacOS
- Open System Preferences: Go to Apple Menu > System Settings > Network.
- Select the current WiFi or Ethernet network where your device is connected and click “Advanced.”
- Locate the “DNS” tab and click the “+” button then enter the DNS addresses you want to use.
- Save Settings: Click “OK” and then “Apply” to save your changes.
- On Android
- Open Wi-Fi Settings: Go to Settings > Network & Internet > Wi-Fi.
- Long-press your connected Wi-Fi network, then tap “Modify network.” Under “Advanced options,” set “IP settings” to “Static,” and then manually enter the DNS addresses.
- Tap “Save” to apply the new DNS settings.
- On iOS
- Open Wi-Fi Settings: Go to Settings > Wi-Fi.
- Tap the “i” icon next to your connected Wi-Fi network. Scroll down to “DNS” and tap “Configure DNS.” Select “Manual” and then add the DNS addresses.
- Tap “Save” to apply the new DNS settings.
- On your Router
- You can also check if you have administrator access to your router and check on the internet for user guides to change the router’s DNS settings.
While changing DNS settings can be effective in bypassing some types of censorship, there are limitations:
- Changing DNS settings only works for DNS-based censorship. If a website is blocked using other methods (e.g., IP blocking, Deep Packet Inspection), changing DNS alone won’t be sufficient.
- Using third-party DNS servers introduces potential privacy and security risks. Always choose a reputable DNS provider to minimize the chances of data interception or logging.
- Some governments and ISPs are aware that users can bypass censorship by changing DNS settings, so they may block access to popular public DNS servers or implement more advanced censorship techniques.
5. USING THE TOR NETWORK
The Onion Router (TOR) is a decentralized network designed to anonymize internet traffic by routing it through multiple volunteer-operated servers (nodes). Tor uses a technique called onion routing, where data is encrypted multiple times and then sent through a series of relay nodes, each of which decrypts one layer of encryption before passing the data to the next node. The final node, called the exit node, decrypts the final layer of data (which is often the innermost layer of the “onion”) and then sends the original data to the intended destination. This layered encryption process ensures that no single node knows both the source and destination of the data, providing anonymity.
Configuring the TOR Browser:
- Visit the official Tor Project website and download the Tor Browser for your operating system.
- Install the browser, launch it, and click “Connect” to establish a connection to the Tor network.
- Once connected, you can browse the internet anonymously, bypassing censorship and protecting your privacy.
Tor Network Structure
- Entry Node: The first node in the Tor network that your data passes through. It knows your IP address but not your final destination.
- Middle Nodes: Intermediate nodes that relay your traffic. They only know the previous and next nodes, making it difficult to trace the path of your data.
- Exit Node: The last node that sends your traffic to its final destination. It knows the destination but not the source.
The TOR network can be accessed by downloading and installing the TOR browser on your device which is a a modified version of Mozilla Firefox that is pre-configured to connect to the Tor network. Here’s how using TOR can help you bypass internet restrictions:
- Internet traffic anonymity: One of the primary ways Tor helps bypass censorship is by anonymizing your internet traffic. Since your data is routed through multiple nodes and encrypted at each step, it’s nearly impossible for censors to determine your true location, identity, or the content you are accessing. This makes it difficult for ISPs or governments to block specific websites or services based on your IP address.
- Bypassing IP-based censorship: Many forms of censorship involve blocking access to certain IP addresses. Tor helps bypass this by routing your traffic through different IP addresses at each step. Because the exit node’s IP address is different from your own, and it’s not easily associated with your identity, you can access websites that might otherwise be blocked in your region.
- Bypassing deep-packet inspection: We mentioned that some advanced censorship systems use Deep Packet Inspection (DPI) to analyze the content of internet traffic and block specific types of data or websites. Tor can bypass DPI because it encrypts your traffic in such a way that DPI systems cannot easily decrypt or analyze the data. Additionally, TOR contains special entry nodes called obfuscated bridges that can disguise Tor traffic to make it look like regular HTTPS traffic, further evading DPI.
- Bypassing geo-restricted content: Since your traffic exits the Tor network through a node in a different country, you can bypass geographic restrictions and censorship to reach content that might otherwise be inaccessible in your country.
- Using TOR Bridges: In regions where access to the Tor network itself is blocked, you can use Tor bridges—unlisted entry points to the Tor network. Bridges help users connect to Tor even when their ISP or government blocks known Tor nodes.
- Using Obfs4 Bridges: These are a type of bridge that uses obfuscation to make Tor traffic look like regular internet traffic, helping to bypass censorship that relies on DPI.
- Requesting Bridges directly from Tor: If you need bridges, Tatua can help you request them from the Tor Project via email or by using the Tor Browser’s built-in bridge fetcher. We can also help configure an unlisted entry point to the Tor network for highly at-risk communities.
- Using TAILS Operating System (Tails OS): For advanced and highly at-risk users, Tails (The Amnesic Incognito Live System) is a Linux-based operating system that routes all internet traffic through Tor by default. It’s designed to be booted from a USB drive, leaving no trace on the host computer, making it ideal for bypassing censorship in highly restrictive environments. Tatua can help you set up and configure Tails OS in a secure flash drive in case you are an at-risk community requiring highly advanced censorship and surveillance circumvention.
While Tor is a powerful tool for bypassing censorship, it does have limitations:
- Tor is slower than regular internet connections due to the multiple relays your traffic passes through. This can make streaming video, downloading large files, or using bandwidth-intensive applications more challenging.
- Exit Node Vulnerabilities: Traffic exiting the Tor network is decrypted at the exit node, the operator of the exit node could potentially see unencrypted data. Therefore, it’s important to use end-to-end encryption (like HTTPS) when using Tor.
- In some cases, ISPs or governments may block access to the Tor network or throttle Tor traffic. While bridges and obfuscation techniques can help, in highly restrictive environments, users may need to combine techniques such as:
- Using Tor over VPN: This is where you connect to a VPN before connecting to Tor which hides the fact that you’re using Tor from your ISP. The VPN encrypts your traffic, making it harder for censors to detect that you’re accessing the Tor network. This can be especially useful in countries where using Tor is itself suspicious.
- Using VPN over Tor: In this setup, you connect to Tor first and then use a VPN. This can be useful for accessing services that block Tor exit nodes or for adding an extra layer of encryption. However, it’s more complex to set up and may reduce anonymity.
- Combining Tor with unlisted nodes + VPN: For users in highly censored environments, combining Tor with obfs4 bridges and a trusted VPN can provide a powerful means to evade detection and access blocked content.




